Refined Fortinet NSE6_FAC-6.4 Exam Price Online
It is more faster and easier to pass the Fortinet NSE6_FAC-6.4 exam by using Validated Fortinet Fortinet NSE 6 - FortiAuthenticator 6.4 questuins and answers. Immediate access to the Up to the minute NSE6_FAC-6.4 Exam and find the same core area NSE6_FAC-6.4 questions with professionally verified answers, then PASS your exam with a high score now.
Free demo questions for Fortinet NSE6_FAC-6.4 Exam Dumps Below:
NEW QUESTION 1
Which interface services must be enabled for the SCEP client to connect to Authenticator?
- A. OCSP
- B. REST API
- C. SSH
- D. HTTP/HTTPS
Answer: D
Explanation:
HTTP/HTTPS are the interface services that must be enabled for the SCEP client to connect to FortiAuthenticator. SCEP stands for Simple Certificate Enrollment Protocol, which is a method of requesting and issuing digital certificates over HTTP or HTTPS. FortiAuthenticator supports SCEP as a certificate authority (CA) and can process SCEP requests from SCEP clients. To enable SCEP on FortiAuthenticator, the HTTP or HTTPS service must be enabled on the interface that receives the SCEP requests.
References:
https://docs.fortinet.com/document/fortiauthenticator/6.4.0/administration-guide/906179/certificate-management
NEW QUESTION 2
You are a Wi-Fi provider and host multiple domains.
How do you delegate user accounts, user groups and permissions per domain when they are authenticating on a single FortiAuthenticator device?
- A. Create realms.
- B. Create user groups
- C. Create multiple directory trees on FortiAuthenticator
- D. Automatically import hosts from each domain as they authenticate.
Answer: A
Explanation:
Realms are a way to delegate user accounts, user groups and permissions per domain when they are authenticating on a single FortiAuthenticator device. A realm is a logical grouping of users and groups based on a common attribute, such as a domain name or an IP address range. Realms allow administrators to apply different authentication policies and settings to different groups of users based on their realm membership.
References:
https://docs.fortinet.com/document/fortiauthenticator/6.4.0/administration-guide/906179/user-management#real
NEW QUESTION 3
When generating a TOTP for two-factor authentication, what two pieces of information are used by the algorithm to generate the TOTP?
- A. UUID and time
- B. Time and seed
- C. Time and mobile location
- D. Time and FortiAuthenticator serial number
Answer: B
Explanation:
TOTP stands for Time-based One-time Password, which is a type of OTP that is generated based on two
pieces of information: time and seed. The time is the current timestamp that is synchronized between the client and the server. The seed is a secret key that is shared between the client and the server. The TOTP algorithm combines the time and the seed to generate a unique and short-lived OTP that can be used for two-factor authentication.
References:
https://docs.fortinet.com/document/fortiauthenticator/6.4.0/administration-guide/906179/two-factor-authenticati
NEW QUESTION 4
Which two capabilities does FortiAuthenticator offer when acting as a self-signed or local CA? (Choose two)
- A. Validating other CA CRLs using OSCP
- B. Importing other CA certificates and CRLs
- C. Merging local and remote CRLs using SCEP
- D. Creating, signing, and revoking of X.509 certificates
Answer: BD
Explanation:
FortiAuthenticator can act as a self-signed or local CA that can issue certificates to users, devices, or other CAs. It can also import other CA certificates and CRLs to trust them and validate their certificates. It can also create, sign, and revoke X.509 certificates for various purposes, such as VPN authentication, web server encryption, or wireless security. It cannot validate other CA CRLs using OCSP or merge local and remote CRLs using SCEP because these are protocols that require communication with external CAs. References: https://docs.fortinet.com/document/fortiauthenticator/6.4/administration-guide/372408/certificate-management
NEW QUESTION 5
Which network configuration is required when deploying FortiAuthenticator for portal services?
- A. FortiAuthenticator must have the REST API access enable on port1
- B. One of the DNS servers must be a FortiGuard DNS server
- C. Fortigate must be setup as default gateway for FortiAuthenticator
- D. Policies must have specific ports open between FortiAuthenticator and the authentication clients
Answer: D
Explanation:
When deploying FortiAuthenticator for portal services, such as guest portal, sponsor portal, user portal or FortiToken activation portal, the network configuration must allow specific ports to be open between FortiAuthenticator and the authentication clients. These ports are: TCP 80 for HTTP access
TCP 80 for HTTP access  TCP 443 for HTTPS access
TCP 443 for HTTPS access  TCP 389 for LDAP access
TCP 389 for LDAP access TCP 636 for LDAPS access
TCP 636 for LDAPS access UDP 1812 for RADIUS authentication
UDP 1812 for RADIUS authentication  UDP 1813 for RADIUS accounting
UDP 1813 for RADIUS accounting
References:
https://docs.fortinet.com/document/fortiauthenticator/6.4.0/administration-guide/906179/portal-services#networ
NEW QUESTION 6
At a minimum, which two configurations are required to enable guest portal services on FortiAuthenticator? (Choose two)
- A. Configuring a portal policy
- B. Configuring at least on post-login service
- C. Configuring a RADIUS client
- D. Configuring an external authentication portal
Answer: AB
Explanation:
enable guest portal services on FortiAuthenticator, you need to configure a portal policy that defines the conditions for presenting the guest portal to users and the authentication methods to use. You also need to configure at least one post-login service that defines what actions to take after a user logs in successfully, such as sending an email confirmation, assigning a VLAN, or creating a user account. Configuring a RADIUS client or an external authentication portal are optional steps that depend on your network setup and requirements. References:
https://docs.fortinet.com/document/fortiauthenticator/6.4/administration-guide/372404/guest-management
NEW QUESTION 7
Which two features of FortiAuthenticator are used for EAP deployment? (Choose two)
- A. Certificate authority
- B. LDAP server
- C. MAC authentication bypass
- D. RADIUS server
Answer: AD
Explanation:
Two features of FortiAuthenticator that are used for EAP deployment are certificate authority and RADIUS server. Certificate authority allows FortiAuthenticator to issue and manage digital certificates for EAP methods that require certificate-based authentication, such as EAP-TLS or PEAP-EAP-TLS. RADIUS server allows FortiAuthenticator to act as an authentication server for EAP methods that use RADIUS as a transport protocol, such as EAP-GTC or PEAP-MSCHAPV2.
References:
https://docs.fortinet.com/document/fortiauthenticator/6.4.0/administration-guide/906179/wireless-802-1x-authen
NEW QUESTION 8
What are three key features of FortiAuthenticator? (Choose three)
- A. Identity management device
- B. Log server
- C. Certificate authority
- D. Portal services
- E. RSSO Server
Answer: ACD
Explanation:
FortiAuthenticator is a user and identity management solution that provides strong authentication, wireless 802.1X authentication, certificate management, RADIUS AAA (authentication, authorization, and accounting), and Fortinet Single Sign-On (FSSO). It also offers portal services for guest management,
self-service password reset, and device registration. It is not a log server or an RSSO server. References:
https://docs.fortinet.com/document/fortiauthenticator/6.4/release-notes
NEW QUESTION 9
Which two types of digital certificates can you create in Fortiauthenticator? (Choose two)
- A. User certificate
- B. Organization validation certificate
- C. Third-party root certificate
- D. Local service certificate
Answer: AD
Explanation:
FortiAuthenticator can create two types of digital certificates: user certificates and local service certificates. User certificates are issued to users or devices for authentication purposes, such as VPN, wireless, or web access. Local service certificates are issued to FortiAuthenticator itself for securing its own services, such as HTTPS, RADIUS, or LDAP.
References:
https://docs.fortinet.com/document/fortiauthenticator/6.4.0/administration-guide/906179/certificate-management
NEW QUESTION 10
What are three key features of FortiAuthenticator? (Choose three)
- A. Identity management device
- B. Log server
- C. Certificate authority
- D. Portal services
- E. RSSO Server
Answer: ACD
Explanation:
FortiAuthenticator is a user and identity management solution that provides strong authentication, wireless 802.1X authentication, certificate management, RADIUS AAA (authentication, authorization, and accounting), and Fortinet Single Sign-On (FSSO). It also offers portal services for guest management,
self-service password reset, and device registration. It is not a log server or an RSSO server. References: https://docs.fortinet.com/document/fortiauthenticator/6.4/release-notes
NEW QUESTION 11
An administrator wants to keep local CA cryptographic keys stored in a central location.
Which FortiAuthenticator feature would provide this functionality?
- A. SCEP support
- B. REST API
- C. Network HSM
- D. SFTP server
Answer: C
Explanation:
Network HSM is a feature that allows FortiAuthenticator to keep local CA cryptographic keys stored in a central location. HSM stands for Hardware Security Module, which is a physical device that provides secure storage and generation of cryptographic keys. Network HSM allows FortiAuthenticator to use an external HSM device to store and manage the private keys of its local CAs, instead of storing them locally on the FortiAuthenticator device.
References:
https://docs.fortinet.com/document/fortiauthenticator/6.4.0/administration-guide/906179/certificate-management
NEW QUESTION 12
A device or user identity cannot be established transparently, such as with non-domain BYOD devices, and allow users to create their own credentialis.
In this case, which user idendity discovery method can Fortiauthenticator use?
- A. Syslog messaging or SAML IDP
- B. Kerberos-base authentication
- C. Radius accounting
- D. Portal authentication
Answer: D
Explanation:
Portal authentication is a user identity discovery method that can be used when a device or user identity cannot be established transparently, such as with non-domain BYOD devices, and allow users to create their own credentials. Portal authentication requires users to enter their credentials on a web page before accessing network resources. The other methods are used for transparent identification of domain devices or users. References:
https://docs.fortinet.com/document/fortiauthenticator/6.4/administration-guide/372406/user-identity-discovery
Examine the screenshot shown in the exhibit.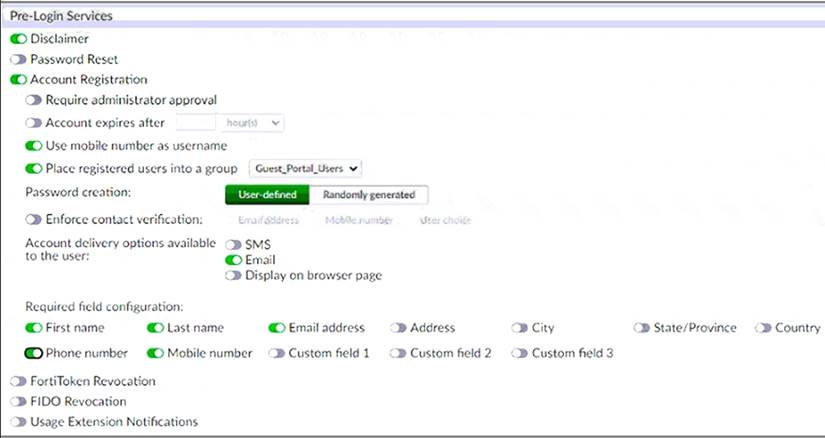
NEW QUESTION 13
Which two statements about the EAP-TTLS authentication method are true? (Choose two)
- A. Uses mutual authentication
- B. Uses digital certificates only on the server side
- C. Requires an EAP server certificate
- D. Support a port access control (wired) solution only
Answer: BC
Explanation:
EAP-TTLS is an authentication method that uses digital certificates only on the server side to establish a secure tunnel between the server and the client. The client does not need a certificate but can use any inner authentication method supported by the server, such as PAP, CHAP, MS-CHAP, or EAP-MD5. EAP-TTLS requires an EAP server certificate that is issued by a trusted CA and installed on the FortiAuthenticator device acting as the EAP server. EAP-TTLS supports both wireless and wired solutions for port access control. References: https://docs.fortinet.com/document/fortiauthenticator/6.4/administration-guide/372412/eap-ttls
NEW QUESTION 14
Which two statement about the RADIUS service on FortiAuthenticator are true? (Choose two)
- A. Two-factor authentication cannot be enforced when using RADIUS authentication
- B. RADIUS users can migrated to LDAP users
- C. Only local users can be authenticated through RADIUS
- D. FortiAuthenticator answers only to RADIUS client that are registered with FortiAuthenticator
Answer: BD
Explanation:
Two statements about the RADIUS service on FortiAuthenticator are true: RADIUS users can be migrated to LDAP users using the RADIUS learning mode feature. This feature allows FortiAuthenticator to learn user credentials from an existing RADIUS server and store them locally as LDAP users for future authentication requests.
RADIUS users can be migrated to LDAP users using the RADIUS learning mode feature. This feature allows FortiAuthenticator to learn user credentials from an existing RADIUS server and store them locally as LDAP users for future authentication requests. FortiAuthenticator answers only to RADIUS clients that are registered with FortiAuthenticator. A RADIUS client is a device that sends RADIUS authentication or accounting requests to FortiAuthenticator. A RADIUS client must be added and configured on FortiAuthenticator before it can communicate with it.
FortiAuthenticator answers only to RADIUS clients that are registered with FortiAuthenticator. A RADIUS client is a device that sends RADIUS authentication or accounting requests to FortiAuthenticator. A RADIUS client must be added and configured on FortiAuthenticator before it can communicate with it.
References:
https://docs.fortinet.com/document/fortiauthenticator/6.4.0/administration-guide/906179/radius-service
NEW QUESTION 15
......
P.S. Easily pass NSE6_FAC-6.4 Exam with 47 Q&As Surepassexam Dumps & pdf Version, Welcome to Download the Newest Surepassexam NSE6_FAC-6.4 Dumps: https://www.surepassexam.com/NSE6_FAC-6.4-exam-dumps.html (47 New Questions)