Pinpoint VMware 2V0-41.23 Prep Online
Our pass rate is high to 98.9% and the similarity percentage between our 2V0-41.23 study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the VMware 2V0-41.23 exam in just one try? I am currently studying for the VMware 2V0-41.23 exam. Latest VMware 2V0-41.23 Test exam practice questions and answers, Try VMware 2V0-41.23 Brain Dumps First.
Check 2V0-41.23 free dumps before getting the full version:
NEW QUESTION 1
A customer is preparing to deploy a VMware Kubernetes solution in an NSX environment. What is the minimum MTU size for the UPLINK profile?
- A. 1500
- B. 1550
- C. 1700
- D. 1650
Answer: C
Explanation:
The minimum MTU size for the UPLINK profile is 1700 bytes. This is because the UPLINK profile is used to configure the physical NICs that connect to the NSX-T overlay network. The overlay network uses geneve encapsulation, which adds an overhead of 54 bytes to the original packet. Therefore, to support a standard MTU of 1500 bytes for the inner packet, the outer packet must have an MTU of at least 1554 bytes. However, VMware recommends adding an extra buffer of 146 bytes to account for possible additional headers or VLAN tags. Therefore, the minimum MTU size for the UPLINK profile is 1700 bytes (1554 + 146). References: : VMware NSX-T Data Center Installation Guide, page 23. : VMware NSX-T Data Center Administration Guide, page 102. : VMware NSX-T Data Center Installation Guide, page 24.
NEW QUESTION 2
Which of the following settings must be configured in an NSX environment before enabling stateful active-active SNAT?
- A. Tier-1 gateway in active-standby mode
- B. Tier-1 gateway in distributed only mode
- C. An Interface Group for the NSX Edge uplinks
- D. A Punting Traffic Group for the NSX Edge uplinks
Answer: C
Explanation:
To enable stateful active-active SNAT on a Tier-0 or Tier-1 gateway, you must configure an Interface Group for the NSX Edge uplinks. An Interface Group is a logical grouping of NSX Edge interfaces that belong to the same failure domain. A failure domain is a set of NSX Edge nodes that share the same physical network infrastructure and are subject to the same network failures. By configuring an Interface Group, you can ensure that the stateful services are distributed across different failure domains and can recover from network failures1
NEW QUESTION 3
What must be configured on Transport Nodes for encapsulation and decapsulation of Geneve protocol?
- A. VXIAN
- B. UDP
- C. STT
- D. TEP
Answer: D
Explanation:
According to the VMware NSX Documentation, TEP stands for Tunnel End Point and is a logical interface that must be configured on transport nodes for encapsulation and decapsulation of Geneve protocol. Geneve is a tunneling protocol that encapsulates the original packet with an outer header that contains metadata such as the virtual network identifier (VNI) and the transport node IP address. TEPs are responsible for adding and removing the Geneve header as the packet traverses the overlay network.
NEW QUESTION 4
Which three data collection sources are used by NSX Network Detection and Response to create correlations/Intrusion campaigns? (Choose three.)
- A. Files and anti-malware (lie events from the NSX Edge nodes and the Security Analyzer
- B. East-West anti-malware events from the ESXi hosts
- C. Distributed Firewall flow data from the ESXi hosts
- D. IDS/IPS events from the ESXi hosts and NSX Edge nodes
- E. Suspicious Traffic Detection events from NSX Intelligence
Answer: ADE
Explanation:
The correct answers are A. Files and anti-malware (file) events from the NSX Edge nodes and the Security Analyzer, D. IDS/IPS events from the ESXi hosts and NSX Edge nodes, and E. Suspicious Traffic Detection events from NSX Intelligence. According to the VMware NSX Documentation3, these are the three data collection sources that are used by NSX Network Detection and Response to create correlations/intrusion campaigns.
The other options are incorrect or not supported by NSX Network Detection and Response. East-West anti-malware events from the ESXi hosts are not collected by NSX Network Detection and
Response3. Distributed Firewall flow data from the ESXi hosts are not used for correlation/intrusion
campaigns by NSX Network Detection and Response3.
https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.2/administration/GUID-14BBE50D-9931-4719-8F
NEW QUESTION 5
Which choice is a valid insertion point for North-South network introspection?
- A. Guest VM vNIC
- B. Partner SVM
- C. Tier-0 gateway
- D. Host Physical NIC
Answer: C
Explanation:
A valid insertion point for North-South network introspection is Tier-0 gateway. North-South network introspection is a service insertion feature that allows third-party network services to be integrated with
NSX. North-South network introspection enables traffic redirection from the uplink of an NSX Edge node to a service chain that consists of one or more service profiles1. The Tier-0 gateway is the logical router that connects the NSX Edge node to the physical network and provides North-South routing and network
services2.
https://docs.vmware.com/en/VMware-NSX/4.1/administration/GUID-D5933474-34A2-4DCE-AE9B-A82FF33
NEW QUESTION 6
When collecting support bundles through NSX Manager, which files should be excluded for potentially containing sensitive information?
- A. Controller Files
- B. Management Files
- C. Core Files
- D. Audit Files
Answer: C
Explanation:
According to the VMware NSX Documentation1, core files and audit logs can contain sensitive information and should be excluded from the support bundle unless requested by VMware technical support. Controller files and management files are not mentioned as containing sensitive information.
NEW QUESTION 7
What needs to be configured on a Tler-0 Gateway lo make NSX Edge Services available to a VM on a VLAN-backed logical switch?
- A. Downlink Interface
- B. VLAN Uplink
- C. Loopback Router Port
- D. Service Interface
Answer: B
Explanation:
To make NSX Edge Services available to a VM on a VLAN-backed logical switch, you need to configure
a VLAN Uplink on the Tier-0 Gateway. A VLAN Uplink is a logical interface that connects the Tier-0 Gateway to the physical network and provides external connectivity for the NSX Edge Services1. A VLAN Uplink can be configured on the NSX Manager UI by selecting Networking > Tier-0 Gateways > Interfaces > Set > Add Interface1.
https://docs.vmware.com/en/VMware-NSX/4.1/administration/GUID-D641380B-4C8E-4C8A-AF64-4261A266
NEW QUESTION 8
An NSX administrator Is treating a NAT rule on a Tler-0 Gateway configured In active-standby high availability mode. Which two NAT rule types are supported for this configuration? (Choose two.)
- A. Reflexive NAT
- B. Destination NAT
- C. 1:1 NAT
- D. Port NAT
- E. Source NAT
Answer: BE
Explanation:
According to the VMware NSX Documentation, these are two NAT rule types that are supported for a tier-0 gateway configured in active-standby high availability mode. NAT stands for Network Address Translation and is a feature that allows you to modify the source or destination IP address of a packet as it passes through a gateway. Destination NAT: This rule type allows you to change the destination IP address of a packet from an external IP address to an internal IP address. You can use this rule type to provide access to your internal servers from external networks using public IP addresses.
Destination NAT: This rule type allows you to change the destination IP address of a packet from an external IP address to an internal IP address. You can use this rule type to provide access to your internal servers from external networks using public IP addresses. Source NAT: This rule type allows you to change the source IP address of a packet from an internal IP address to an external IP address. You can use this rule type to provide access to external networks from your internal servers using public IP addresses.
Source NAT: This rule type allows you to change the source IP address of a packet from an internal IP address to an external IP address. You can use this rule type to provide access to external networks from your internal servers using public IP addresses.
NEW QUESTION 9
A company security policy requires all users to log Into applications using a centralized authentication system. Which two authentication, authorization, and accounting (AAA) systems are available when Integrating NSX with VMware Identity Manager? (Choose two.)
- A. RADII 2.0
- B. Keyoen Enterprise
- C. RSA SecurelD
- D. LDAP and OpenLDAP based on Active Directory (AD)
- E. SecureDAP
Answer: CD
Explanation:
NSX supports two types of authentication, authorization, and accounting (AAA) systems when integrating with VMware Identity Manager: RSA SecurID and LDAP and OpenLDAP based on Active Directory (AD). RSA SecurID is a two-factor authentication system that uses a token-based approach to verify the identity of users. LDAP and OpenLDAP based on AD are directory services that store and manage user information and credentials. Both systems can be used to provide centralized authentication for users who want to access applications in an NSX environment .
https://blogs.vmware.com/networkvirtualization/2017/11/remote-user-authentication-and-rbac-with-nsx-t.html
NEW QUESTION 10
Which two statements describe the characteristics of an Edge Cluster in NSX? (Choose two.)
- A. Can have a maximum of 8 edge nodes
- B. Can have a maximum of 10 edge nodes
- C. Must have only active-active edge nodes
- D. Can contain multiple types of edge nodes (VM or bare metal)
- E. Must contain only one type of edge nodes (VM or bare metal)
Answer: AE
Explanation:
Two statements that describe the characteristics of an Edge Cluster in NSX are: An Edge Cluster can have a maximum of 8 edge nodes2. This is the upper limit for scaling out the Edge Cluster and providing high availability and load balancing for network services.
An Edge Cluster can have a maximum of 8 edge nodes2. This is the upper limit for scaling out the Edge Cluster and providing high availability and load balancing for network services. An Edge Cluster must contain only one type of edge nodes (VM or bare metal)3. This is because different types of edge nodes have different performance and resource requirements, and mixing them in the same cluster can cause inconsistency and instability. The other options are incorrect because they do not describe the characteristics of an Edge Cluster in NSX. An Edge Cluster can have either
An Edge Cluster must contain only one type of edge nodes (VM or bare metal)3. This is because different types of edge nodes have different performance and resource requirements, and mixing them in the same cluster can cause inconsistency and instability. The other options are incorrect because they do not describe the characteristics of an Edge Cluster in NSX. An Edge Cluster can have either
active-active or active-standby edge nodes, depending on the configuration and services4. An Edge Cluster cannot contain multiple types of edge nodes, as explained above. References: Enhanced NSX Edge and Networking Services in NSX 4.0.1.1, NSX Edge Installation Requirements, NSX-T Edge Node Cluster
NEW QUESTION 11
NSX improves the security of today's modern workloads by preventing lateral movement, which feature of NSX can be used to achieve this?
- A. Network Segmentation
- B. Virtual Security Zones
- C. Edge Firewalling
- D. Dynamic Routing
Answer: A
Explanation:
According to the web search results, network segmentation is a feature of NSX that improves the security of today’s modern workloads by preventing lateral movement. Lateral movement is a technique used by attackers to move from one compromised system to another within a network, exploiting vulnerabilities or credentials . Network segmentation prevents lateral movement by dividing a network into smaller segments or zones, each with its own security policies and controls. This way, if one segment is compromised, the attacker cannot access other segments or resources . NSX enables network segmentation by using micro-segmentation, which applies granular firewall rules at the virtual machine level, regardless of the physical network topology .
NEW QUESTION 12
Which troubleshooting step will resolve an error with code 1001 during the configuration of a time-based firewall rule?
- A. Reinstalling the NSX VIBs on the ESXi host.
- B. Restarting the NTPservice on the ESXi host.
- C. Changing the lime zone on the ESXi host.
- D. Reconfiguring the ESXI host with a local NTP server.
Answer: B
Explanation:
According to the web search results, error code 1001 is related to a time synchronization issue between the ESXi host and the NSX Manager. This can cause problems when configuring a time-based firewall rule, which requires the ESXi host and the NSX Manager to have the same time zone and NTP server settings . To resolve this error, you need to restart the NTP service on the ESXi host to synchronize the time with the NSX Manager. You can use the following command to restart the NTP service on the ESXi host:
/etc/init.d/ntpd restart
The other options are not valid solutions for this error. Reinstalling the NSX VIBs on the ESXi host will not fix the time synchronization issue. Changing the time zone on the ESXi host may cause more discrepancies with the NSX Manager. Reconfiguring the ESXi host with a local NTP server may not be compatible with the NSX Manager’s NTP server.
NEW QUESTION 13
Which is an advantages of a L2 VPN In an NSX 4.x environment?
- A. Enables Multi-Cloud solutions
- B. Achieve better performance
- C. Enables VM mobility with re-IP
- D. Use the same broadcast domain
Answer: D
Explanation:
L2 VPN is a feature of NSX that allows extending Layer 2 networks across different sites or clouds over an IPsec tunnel. L2 VPN has an advantage of enabling VM mobility with re-IP, which means that VMs can be moved from one site to another without changing their IP addresses or network configurations. This is possible because L2 VPN allows both sites to use the same broadcast domain, which means that they share the same subnet and VLAN .
NEW QUESTION 14
When a stateful service is enabled for the first lime on a Tier-0 Gateway, what happens on the NSX Edge node'
- A. SR is instantiated and automatically connected with DR.
- B. DR Is instantiated and automatically connected with SR.
- C. SR and DR Is instantiated but requites manual connection.
- D. SR and DR doesn't need to be connected to provide any stateful services.
Answer: A
Explanation:
The answer is A. SR is instantiated and automatically connected with DR.
SR stands for Service Router and DR stands for Distributed Router. They are components of the NSX Edge node that provide different functions1
The SR is responsible for providing stateful services such as NAT, firewall, load balancing, VPN, and DHCP. The DR is responsible for providing distributed routing and switching between logical segments and the physical network1
When a stateful service is enabled for the first time on a Tier-0 Gateway, the NSX Edge node automatically creates an SR instance and connects it with the existing DR instance. This allows the stateful service to be applied to the traffic that passes through the SR before reaching the DR2
According to the VMware NSX 4.x Professional Exam Guide, understanding the SR and DR components and their functions is one of the exam objectives3
To learn more about the SR and DR components and how they work on the NSX Edge node, you can refer to the following resources: VMware NSX Documentation: NSX Edge Components 1
VMware NSX Documentation: NSX Edge Components 1  VMware NSX 4.x Professional: NSX Edge Architecture
VMware NSX 4.x Professional: NSX Edge Architecture  VMware NSX 4.x Professional: NSX Edge Routing
VMware NSX 4.x Professional: NSX Edge Routing
NEW QUESTION 15
Where is the insertion point for East-West network introspection?
- A. Tier-0 router
- B. Partner SVM
- C. Guest VM vNIC
- D. Host Physical NIC
Answer: C
Explanation:
The insertion point for East-West network introspection is the Guest VM vNIC. Network introspection is a service insertion feature that allows third-party network services to be integrated with NSX. Network introspection enables traffic redirection from the Guest VM vNIC to a service virtual machine (SVM) that runs the partner service. The SVM can then inspect, monitor, or modify the traffic before sending it back to the original destination1. The other options are incorrect because they are not the insertion points for East-West network introspection. The Tier-0 router is used for North-South routing and network services. The partner SVM is the service virtual machine that runs the partner service, not the insertion point. The host physical NIC is not involved in network introspection. References: Network Introspection Settings
NEW QUESTION 16
An administrator needs to download the support bundle for NSX Manager. Where does the administrator download the log bundle from?
- A. System > Utilities > Tools
- B. System > Support Bundle
- C. System > Settings > Support Bundle
- D. System > Settings
Answer: B
Explanation:
According to the VMware NSX Documentation, this is where you can download the support bundle for NSX Manager from the NSX UI: System > Support Bundle: This option allows you to download a support bundle that contains logs, configuration files, and diagnostic information from your NSX Manager node and cluster. You can use this option to troubleshoot issues or provide information to VMware support.
System > Support Bundle: This option allows you to download a support bundle that contains logs, configuration files, and diagnostic information from your NSX Manager node and cluster. You can use this option to troubleshoot issues or provide information to VMware support.
https://docs.vmware.com/en/VMware-vSphere/7.0/vmware-vsphere-with-tanzu/GUID-794C691E-B950-4838-9 https://docs.vmware.com/en/VMware-NSX/4.1/administration/GUID-73D9AF0D-4000-4EF2-AC66-6572AD1
NEW QUESTION 17
Sort the rule processing steps of the Distributed Firewall. Order responses from left to right.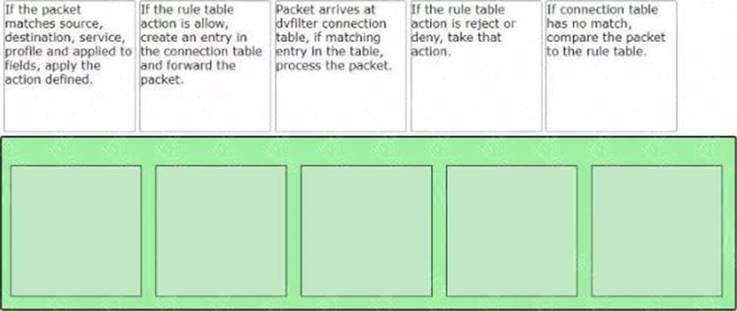
Solution:
The correct order of the rule processing steps of the Distributed Firewall is as follows:
 Packet arrives at vfilter connection table. If matching entry in the table, process the packet.
Packet arrives at vfilter connection table. If matching entry in the table, process the packet.  If connection table has no match, compare the packet to the rule table.
If connection table has no match, compare the packet to the rule table. If the rule table action is allow, create an entry in the connection table and forward the packet.
If the rule table action is allow, create an entry in the connection table and forward the packet. If the rule table action is reject or deny, take that action.
If the rule table action is reject or deny, take that action.This order is based on the description of how the Distributed Firewall works in the web search results1. The first step is to check if there is an existing connection entry for the packet in the vfilter connection table, which is a cache of flow entries for rules with an allow action. If there is a match, the packet is processed according to the connection entry. If there is no match, the packet is compared to the rule table, which contains all the security policy rules. The rules are evaluated from top to bottom until a match is found. The match criteria include source, destination, service, profile and applied to fields. The action defined by the matching rule is applied to the packet. The action can be allow, reject or deny. If the action is allow, a new connection entry is created for the packet and the packet is forwarded to its destination. If the action is reject or deny, the packet is dropped and an ICMP message or a TCP reset message is sent back to the source.
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 18
Refer to the exhibit.
An administrator would like to change the private IP address of the NAT VM I72.l6.101.il to a public address of 80.80.80.1 as the packets leave the NAT-Segment network.
Which type of NAT solution should be implemented to achieve this?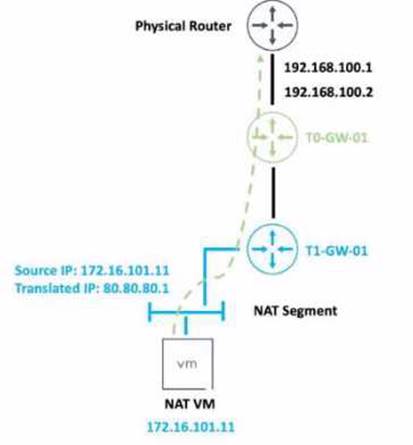
- A. DNAT
- B. SNAT
- C. Reflexive NAT
- D. NAT64
Answer: B
Explanation:
SNAT stands for Source Network Address Translation. It is a type of NAT that translates the source IP address of outgoing packets from a private address to a public address. SNAT is used to allow hosts in a private network to access the internet or other public networks1
In the exhibit, the administrator wants to change the private IP address of the NAT VM 172.16.101.11 to a public address of 80.80.80.1 as the packets leave the NAT-Segment network. This is an example of SNAT, as the source IP address is modified before the packets are sent to an external network.
According to the VMware NSX 4.x Professional Exam Guide, SNAT is one of the topics covered in the exam objectives2
To learn more about SNAT and how to configure it in VMware NSX, you can refer to the following resources:  VMware NSX Documentation: NAT 3
VMware NSX Documentation: NAT 3 VMware NSX 4.x Professional: NAT Configuration 4
VMware NSX 4.x Professional: NAT Configuration 4  VMware NSX 4.x Professional: NAT Troubleshooting 5
VMware NSX 4.x Professional: NAT Troubleshooting 5
https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.2/administration/GUID-7AD2C384-4303-4D6C-A
NEW QUESTION 19
Which field in a Tier-1 Gateway Firewall would be used to allow access for a collection of trustworthy web sites?
- A. Source
- B. Profiles -> Context Profiles
- C. Destination
- D. Profiles -> L7 Access Profile
Answer: D
Explanation:
The field in a Tier-1 Gateway Firewall that would be used to allow access for a collection of trustworthy web sites is Profiles -> L7 Access Profile. This field allows the user to create a Layer 7 access profile that defines list of allowed or blocked URLs based on categories, reputation, or custom entries1. The user can then apply the L7 access profile to a firewall rule to control the traffic based on the URL filtering criteria1. The other options are incorrect because they are not related to URL filtering. The Source field specifies the source IP address or group of the firewall rule1. The Destination field specifies the destination IP address or group of the firewall rule1. The Profiles -> Context Profiles field allows the user to create a context profile that defines a list of application signatures or attributes that can be used to identify and classify network
traffic1. References: Gateway Firewall
NEW QUESTION 20
Which command on ESXI is used to verify the Local Control Plane connectivity with Central Control Plane?
A)
B)
C)
D)
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: B
Explanation:
According to the web search results, the command that is used to verify the Local Control Plane (LCP) connectivity with Central Control Plane (CCP) on ESXi is get control-cluster status. This command displays the status of the LCP and CCP components on the ESXi host, such as the LCP agent, CCP client, CCP server, and CCP connection. It also shows the IP address and port number of the CCP server that the LCP agent is connected to. If the LCP agent or CCP client are not running or not connected, it means that there is a problem with the LCP connectivity .
NEW QUESTION 21
......
P.S. Easily pass 2V0-41.23 Exam with 106 Q&As Dumps-files.com Dumps & pdf Version, Welcome to Download the Newest Dumps-files.com 2V0-41.23 Dumps: https://www.dumps-files.com/files/2V0-41.23/ (106 New Questions)