Refresh 156-915.77 Dumps For Check Point Certified Security Expert Update Blade Certification
Our pass rate is high to 98.9% and the similarity percentage between our 156-915.77 study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the CheckPoint 156-915.77 exam in just one try? I am currently studying for the CheckPoint 156-915.77 exam. Latest CheckPoint 156-915.77 Test exam practice questions and answers, Try CheckPoint 156-915.77 Brain Dumps First.
Online CheckPoint 156-915.77 free dumps demo Below:
NEW QUESTION 1
Where does the security administrator activate Identity Awareness within SmartDashboard?
- A. Gateway Object > General Properties
- B. Security Management Server > Identity Awareness
- C. Policy > Global Properties > Identity Awareness
- D. LDAP Server Object > General Properties
Answer: A
NEW QUESTION 2
Which file defines the fields for each object used in the file objects.C (color, num/string, default value…)?
- A. $FWDIR/conf/classes.C
- B. $FWDIR/conf/scheam.C
- C. $FWDIR/conf/fields.C
- D. $FWDIR/conf/table.C
Answer: A
NEW QUESTION 3
Which operating systems are supported by a Check Point Security Gateway on an open server? Select MOST complete list.
- A. Sun Solaris, Red Hat Enterprise Linux, Check Point SecurePlatform, IPSO, Microsoft Windows
- B. Check Point GAiA and SecurePlatform, and Microsoft Windows
- C. Check Point GAiA, Microsoft Windows, Red Hat Enterprise Linux, Sun Solaris, IPSO
- D. Check Point GAiA and SecurePlatform, IPSO, Sun Solaris, Microsoft Windows
Answer: B
NEW QUESTION 4
Your R77 primary Security Management Server is installed on GAiA. You plan to schedule the Security Management Server to run fw logswitch automatically every 48 hours. How do you create this schedule?
- A. On a GAiA Security Management Server, this can only be accomplished by configuring the command fw logswitch via the cron utility.
- B. Create a time object, and add 48 hours as the interva
- C. Open the primary Security Management Server object’s Logs and Masters window, enable Schedule log switch, and select the Time object.
- D. Create a time object, and add 48 hours as the interva
- E. Open the Security Gateway object's Logs and Masters window, enable Schedule log switch, and select the Time object.
- F. Create a time object, and add 48 hours as the interva
- G. Select that time object’s Global Properties > Logs and Masters window, to schedule a logswitch.
Answer: B
NEW QUESTION 5
When migrating the SmartEvent data base from one server to another, the first step is to back up the files on the original server. Which of the following commands should you run to back up the SmartEvent data base?
- A. migrate export
- B. eva_db_backup
- C. snapshot
- D. backup
Answer: B
NEW QUESTION 6
You find that Gateway fw2 can NOT be added to the cluster object. What are possible reasons for that?
Exhibit: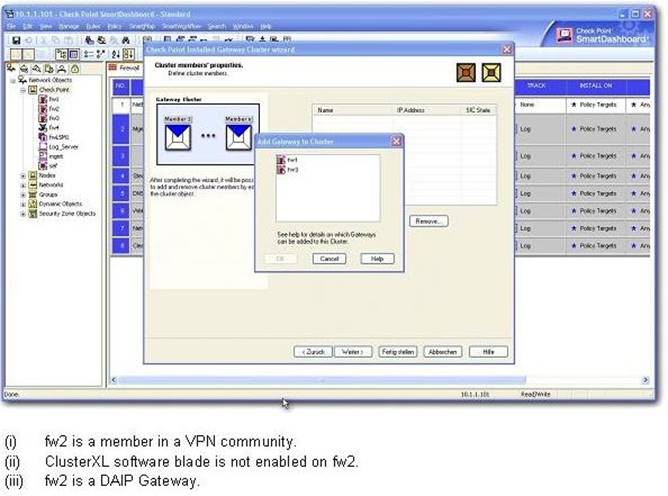
1) fw2 is a member in a VPN community.
2) ClusterXL software blade is not enabled on fw2.
3) fw2 is a DAIP Gateway.
- A. 2 or 3
- B. 1 or 2
- C. 1 or 3
- D. All
Answer: C
NEW QUESTION 7
CORRECT TEXT
Fill in the blank. To remove site-to-site IKE and IPSEC keys you would enter command ____ and select the option to delete all IKE and IPSec SA’s.
Solution:
vpn tu
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 8
10.10.x is configured for Hide NAT behind the Security Gateway’s external interface.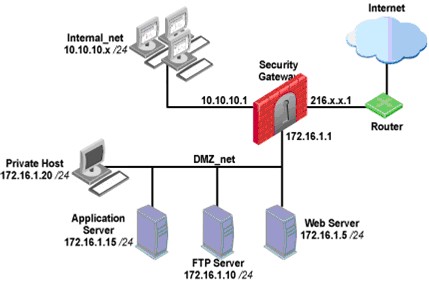
What is the best configuration for 10.10.10.x users to access the DMZ servers, using the DMZ servers’ public IP addresses?
- A. When connecting to internal network 10.10.10.x, configure Hide NAT for the DMZ network behind the Security Gateway DMZ interface.
- B. When the source is the internal network 10.10.10.x, configure manual static NAT rules to translate the DMZ servers.
- C. When connecting to the Internet, configure manual Static NAT rules to translate the DMZ servers.
- D. When trying to access DMZ servers, configure Hide NAT for 10.10.10.x behind the DMZ’s interface.
Answer: B
NEW QUESTION 9
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to
HR servers to designated IP addresses to minimize malware infection and unauthorized access risks. Thus, the gateway policy permits access only from John's desktop which is assigned an IP address 10.0.0.19 via DHCP.
John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but that limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his laptop. He wants to move around the organization and continue to have access to the HR Web Server.
To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources installs the policy.
2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any machine and from any location.
John plugged in his laptop to the network on a different network segment and he is not able to connect. How does he solve this problem?
- A. John should install the Identity Awareness Agent
- B. The firewall admin should install the Security Policy
- C. John should lock and unlock the computer
- D. Investigate this as a network connectivity issue
Answer: B
NEW QUESTION 10
Your perimeter Security Gateway’s external IP is 200.200.200.3. Your network diagram shows: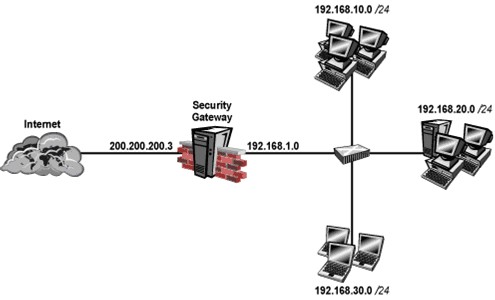
Required: Allow only network 192.168.10.0 and 192.168.20.0 to go out to the Internet, using 200.200.200.5.
The local network 192.168.1.0/24 needs to use 200.200.200.3 to go out to the Internet. Assuming you enable all the settings in the NAT page of Global Properties, how could you achieve these requirements?
- A. Create network objects for 192.168.10.0/24 and 192.168.20.0/24. Enable Hide NAT on both network objects, using 200.200.200.5 as hiding IP addres
- B. Add an ARP entry for 200.200.200.3 for the MAC address of 200.200.200.5.
- C. Create an Address Range object, starting from 192.168.10.1 to 192.168.20.254. Enable Hide NAT on the NAT page of the address range objec
- D. Enter Hiding IP address 200.200.200.5. Add an ARP entry for 200.200.200.5 for the MAC address of 200.200.200.3.
- E. Create a network object 192.168.0.0/16. Enable Hide NAT on the NAT pag
- F. Enter 200.200.200.5 as the hiding IP addres
- G. Add an ARP entry for 200.200.200.5 for the MAC address of 200.200.200.3.
- H. Create two network objects: 192.168.10.0/24 and 192.168.20.0/24. Add the two network objects to a group objec
- I. Create a manual NAT rule like the following: Original source - group object; Destination - any; Service - any; Translated source - 200.200.200.5; Destination - original; Service - original.
Answer: B
NEW QUESTION 11
Update the topology in the cluster object for the cluster and both members.
Solution:
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 12
All R77 Security Servers can perform authentication with the exception of one. Which of the Security Servers can NOT perform authentication?
- A. FTP
- B. SMTP
- C. HTTP
- D. RLOGIN
Answer: B
NEW QUESTION 13
CORRECT TEXT
Type the full cphaprob command and syntax that will show full synchronization status.
Solution:
cphaprob -i list
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 14
Which of the following statements accurately describes the command snapshot?
- A. snapshot creates a full OS-level backup, including network-interface data, Check Point product information, and configuration settings during an upgrade of a GAiA Security Gateway.
- B. snapshot creates a Security Management Server full system-level backup on any OS.
- C. snapshot stores only the system-configuration settings on the Gateway.
- D. A Gateway snapshot includes configuration settings and Check Point product information from the remote Security Management Server.
Answer: A
NEW QUESTION 15
CORRECT TEXT
MultiCorp is located in Atlanta. It has a branch office in Europe, Asia, and Africa. Each location has its own AD controller for local user login. How many ADqueries have to be configured?
Solution:
4
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 16
How can you check whether IP forwarding is enabled on an IP Security Appliance?
- A. clish -c show routing active enable
- B. cat /proc/sys/net/ipv4/ip_forward
- C. echo 1 > /proc/sys/net/ipv4/ip_forward
- D. ipsofwd list
Answer: D
NEW QUESTION 17
......
100% Valid and Newest Version 156-915.77 Questions & Answers shared by DumpSolutions.com, Get Full Dumps HERE: https://www.dumpsolutions.com/156-915.77-dumps/ (New 203 Q&As)