What Downloadable 156-915.77 Answers Is
Our pass rate is high to 98.9% and the similarity percentage between our 156-915.77 study guide and real exam is 90% based on our seven-year educating experience. Do you want achievements in the CheckPoint 156-915.77 exam in just one try? I am currently studying for the CheckPoint 156-915.77 exam. Latest CheckPoint 156-915.77 Test exam practice questions and answers, Try CheckPoint 156-915.77 Brain Dumps First.
Also have 156-915.77 free dumps questions for you:
NEW QUESTION 1
You enable Automatic Static NAT on an internal host node object with a private IP address of 10.10.10.5, which is NATed into 216.216.216.5. (You use the default settings in Global Properties / NAT.)
When you run fw monitor on the R77 Security Gateway and then start a new HTTP connection from host 10.10.10.5 to browse the Internet, at what point in the monitor output will you observe the HTTP SYN-ACK packet translated from 216.216.216.5 back into 10.10.10.5?
- A. o=outbound kernel, before the virtual machine
- B. I=inbound kernel, after the virtual machine
- C. O=outbound kernel, after the virtual machine
- D. i=inbound kernel, before the virtual machine
Answer: B
NEW QUESTION 2
You have created a Rule Base for firewall, websydney. Now you are going to create a new policy package with security and address translation rules for a second Gateway.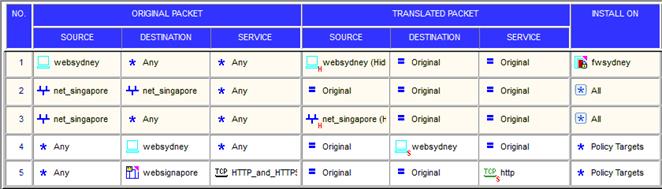
What is TRUE about the new package’s NAT rules?
- A. Rules 1, 2, 3 will appear in the new package.
- B. Only rule 1 will appear in the new package.
- C. NAT rules will be empty in the new package.
- D. Rules 4 and 5 will appear in the new package.
Answer: A
NEW QUESTION 3
Which command line interface utility allows the administrator to verify the Security Policy name and timestamp currently installed on a firewall module?
- A. cpstat fwd
- B. fw ver
- C. fw stat
- D. fw ctl pstat
Answer: C
NEW QUESTION 4
Your company is running Security Management Server R77 on GAiA, which has been migrated through each version starting from Check Point 4.1. How do you add a new administrator account?
- A. Using SmartDashboard, under Users, select Add New Administrator
- B. Using SmartDashboard or cpconfig
- C. Using the Web console on GAiA under Product configuration, select Administrators
- D. Using cpconfig on the Security Management Server, choose Administrators
Answer: A
NEW QUESTION 5
You have three servers located in a DMZ, using private IP addresses. You want internal users from 10.10.10.x to access the DMZ servers by public IP addresses. Internal_net
Solution:
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 6
CORRECT TEXT
Type the command and syntax to view critical devices on a cluster member in a ClusterXL environment.
Solution:
cphaprob -ia list
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 7
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to designated IP addresses to minimize malware infection and unauthorized access risks. Thus, the gateway policy permits access only from John's desktop which is assigned a static IP address 10.0.0.19.
John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but that limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his laptop with a static IP (10.0.0.19). He wants to move around the organization and continue to have access to the HR Web Server.
To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources installs the policy.
2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any machine and from any location.
What should John do when he cannot access the web server from a different personal computer?
- A. John should lock and unlock his computer
- B. Investigate this as a network connectivity issue
- C. The access should be changed to authenticate the user instead of the PC
- D. John should install the Identity Awareness Agent
Answer: C
NEW QUESTION 8
When restoring R77 using the command upgrade_import, which of the following items are NOT restored?
- A. SIC Certificates
- B. Licenses
- C. Route tables
- D. Global properties
Answer: C
NEW QUESTION 9
You are MegaCorp’s Security Administrator. There are various network objects which must be NATed. Some of them use the Automatic Hide NAT method, while others use the Automatic Static NAT method. What is the rule order if both methods are used together? Give the BEST answer.
- A. The Administrator decides the rule order by shifting the corresponding rules up and down.
- B. The Static NAT rules have priority over the Hide NAT rules and the NAT on a node has priority over the NAT on a network or an address range.
- C. The Hide NAT rules have priority over the Static NAT rules and the NAT on a node has priority over the NAT on a network or an address range.
- D. The rule position depends on the time of their creatio
- E. The rules created first are placed at the top; rules created later are placed successively below the others.
Answer: B
NEW QUESTION 10
When configuring numbered VPN Tunnel Interfaces (VTIs) in a clustered environment, what issues need to be considered?
1) Each member must have a unique source IP address.
2) Every interface on each member requires a unique IP address.
3) All VTI's going to the same remote peer must have the same name.
4) Cluster IP addresses are required.
- A. 1, 2, and 4
- B. 2 and 3
- C. 1, 2, 3 and 4
- D. 1, 3, and 4
Answer: C
NEW QUESTION 11
You want to implement Static Destination NAT in order to provide external, Internet users access to an internal Web Server that has a reserved (RFC 1918) IP address. You have an unused valid IP address on the network between your Security Gateway and ISP router. You control the router that sits between the firewall external interface and the Internet.
What is an alternative configuration if proxy ARP cannot be used on your Security Gateway?
- A. Publish a proxy ARP entry on the ISP router instead of the firewall for the valid IP address.
- B. Place a static ARP entry on the ISP router for the valid IP address to the firewall's external address.
- C. Publish a proxy ARP entry on the internal Web server instead of the firewall for the valid IP address.
- D. Place a static host route on the firewall for the valid IP address to the internal Web server.
Answer: B
NEW QUESTION 12
Charles requests a Website while using a computer not in the net_singapore network.
What is TRUE about his location restriction?
- A. Source setting in Source column always takes precedence.
- B. Source setting in User Properties always takes precedence.
- C. As location restrictions add up, he would be allowed from net_singapore and net_sydney.
- D. It depends on how the User Auth object is configured; whether User Properties or Source Restriction takes precedence.
Answer: D
NEW QUESTION 13
Assume you are a Security Administrator for ABCTech. You have allowed authenticated access to users from Mkting_net to Finance_net. But in the user’s properties, connections are only permitted within Mkting_net. What is the BEST way to resolve this conflict?
- A. Select Ignore Database in the Action Properties window.
- B. Permit access to Finance_net.
- C. Select Intersect with user database in the Action Properties window.
- D. Select Intersect with user database or Ignore Database in the Action Properties window.
Answer: D
NEW QUESTION 14
Peter is your new Security Administrator. On his first working day, he is very nervous and enters the wrong password three times. His account is locked. What can be done to unlock Peter’s account? Give the BEST answer.
- A. You can unlock Peter’s account by using the command fwm lock_admin -u Peter on the Security Management Server.
- B. You can unlock Peter’s account by using the command fwm unlock_admin -u Peter on the Security Management Server
- C. It is not possible to unlock Peter’s accoun
- D. You have to install the firewall once again or abstain from Peter’s help.
- E. You can unlock Peter’s account by using the command fwm unlock_admin -u Peter on the Security Gateway.
Answer: A
NEW QUESTION 15
In SmartDashboard, Translate destination on client side is checked in Global Properties. When Network Address Translation is used:
- A. It is not necessary to add a static route to the Gateway’s routing table.
- B. It is necessary to add a static route to the Gateway’s routing table.
- C. The Security Gateway’s ARP file must be modified.
- D. VLAN tagging cannot be defined for any hosts protected by the Gateway.
Answer: A
NEW QUESTION 16
Re-enable "Cluster membership" on the Gateway.
Solution:
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 17
......
Thanks for reading the newest 156-915.77 exam dumps! We recommend you to try the PREMIUM Certleader 156-915.77 dumps in VCE and PDF here: https://www.certleader.com/156-915.77-dumps.html (203 Q&As Dumps)