The Secret Of Paloalto-Networks PCCET Preparation Labs
Proper study guides for Up to the immediate present Paloalto-Networks Palo Alto Networks Certified Cybersecurity Entry-level Technician certified begins with Paloalto-Networks PCCET preparation products which designed to deliver the Printable PCCET questions by making you pass the PCCET test at your first time. Try the free PCCET demo right now.
Online Paloalto-Networks PCCET free dumps demo Below:
NEW QUESTION 1
Which Palo Alto Networks subscription service complements App-ID by enabling you to configure the next-generation firewall to identify and control access to websites and to protect your organization from websites hosting malware and phishing pages?
- A. Threat Prevention
- B. DNS Security
- C. WildFire
- D. URL Filtering
Answer: D
NEW QUESTION 2
What is required for a SIEM to operate correctly to ensure a translated flow from the system of interest to the SIEM data lake?
- A. connectors and interfaces
- B. infrastructure and containers
- C. containers and developers
- D. data center and UPS
Answer: A
NEW QUESTION 3
Which type of LAN technology is being displayed in the diagram?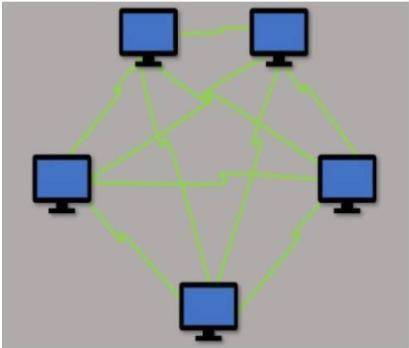
- A. Star Topology
- B. Spine Leaf Topology
- C. Mesh Topology
- D. Bus Topology
Answer: C
NEW QUESTION 4
Which option would be an example of PII that you need to prevent from leaving your enterprise network?
- A. Credit card number
- B. Trade secret
- C. National security information
- D. A symmetric encryption key
Answer: A
NEW QUESTION 5
In which step of the cyber-attack lifecycle do hackers embed intruder code within seemingly innocuous files?
- A. weaponization
- B. reconnaissance
- C. exploitation
- D. delivery
Answer: D
NEW QUESTION 6
Which type of Software as a Service (SaaS) application provides business benefits, is fast to deploy, requires minimal cost and is infinitely scalable?
- A. Benign
- B. Tolerated
- C. Sanctioned
- D. Secure
Answer: C
NEW QUESTION 7
Which characteristic of serverless computing enables developers to quickly deploy application code?
- A. Uploading cloud service autoscaling services to deploy more virtual machines to run their application code based on user demand
- B. Uploading the application code itself, without having to provision a full container image or any OS virtual machine components
- C. Using cloud service spot pricing to reduce the cost of using virtual machines to run their application code
- D. Using Container as a Service (CaaS) to deploy application containers to run their code.
Answer: A
NEW QUESTION 8
Which Palo Alto Networks tools enable a proactive, prevention-based approach to network automation that accelerates security analysis?
- A. MineMeld
- B. AutoFocus
- C. WildFire
- D. Cortex XDR
Answer: D
NEW QUESTION 9
Which Palo Alto Networks tool is used to prevent endpoint systems from running malware executables such as viruses, trojans, and rootkits?
- A. Expedition
- B. Cortex XDR
- C. AutoFocus
- D. App-ID
Answer: B
NEW QUESTION 10
Which organizational function is responsible for security automation and eventual vetting of the solution to help ensure consistency through machine-driven responses to security issues?
- A. NetOps
- B. SecOps
- C. SecDevOps
- D. DevOps
Answer: B
NEW QUESTION 11
Which two network resources does a directory service database contain? (Choose two.)
- A. Services
- B. /etc/shadow files
- C. Users
- D. Terminal shell types on endpoints
Answer: AC
NEW QUESTION 12
Why have software developers widely embraced the use of containers?
- A. Containers require separate development and production environments to promote authentic code.
- B. Containers share application dependencies with other containers and with their host computer.
- C. Containers simplify the building and deploying of cloud native applications.
- D. Containers are host specific and are not portable across different virtual machine hosts.
Answer: C
NEW QUESTION 13
Which attacker profile uses the internet to recruit members to an ideology, to train them, and to spread fear and include panic?
- A. Cybercriminals
- B. state-affiliated groups
- C. hacktivists
- D. cyberterrorists
Answer: D
NEW QUESTION 14
DRAG DROP
Match the IoT connectivity description with the technology.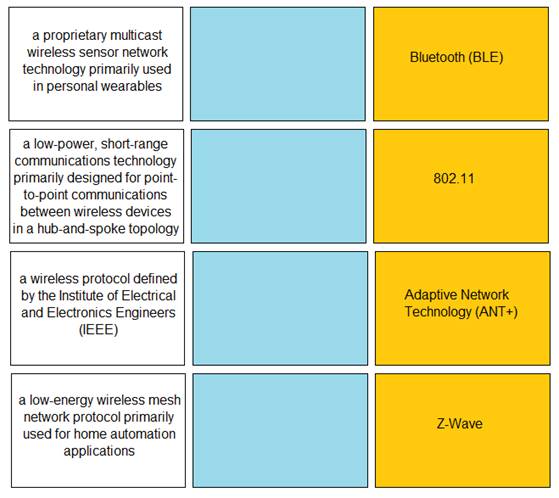
Solution:
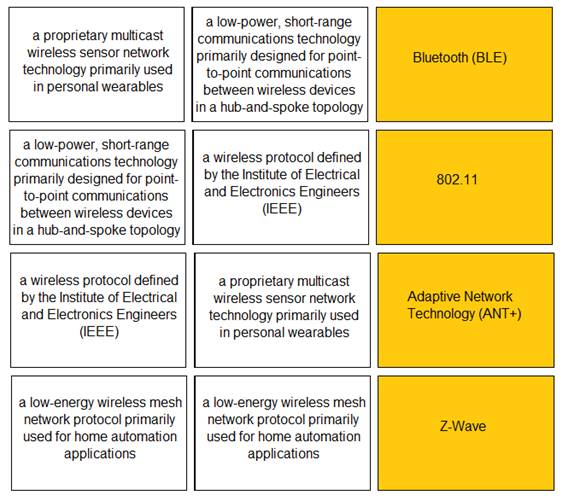
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 15
DRAG DROP
Order the OSI model with Layer7 at the top and Layer1 at the bottom.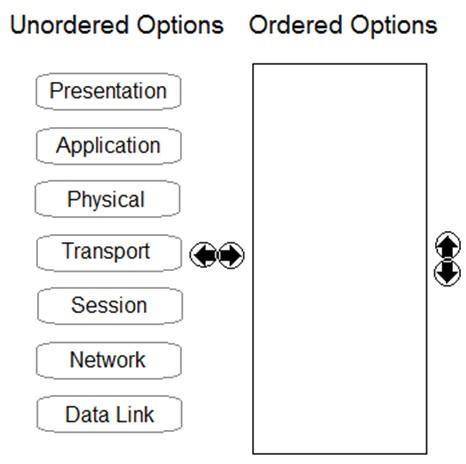
Solution:
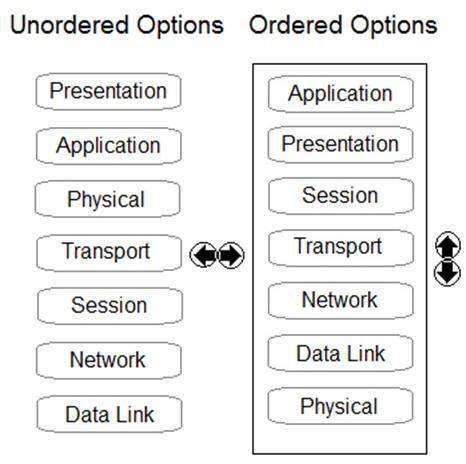
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 16
What is a key advantage and key risk in using a public cloud environment?
- A. Multi-tenancy
- B. Dedicated Networks
- C. Dedicated Hosts
- D. Multiplexing
Answer: A
NEW QUESTION 17
......
Thanks for reading the newest PCCET exam dumps! We recommend you to try the PREMIUM Certleader PCCET dumps in VCE and PDF here: https://www.certleader.com/PCCET-dumps.html (75 Q&As Dumps)