How Many Questions Of PT0-002 Exams
we provide 100% Correct CompTIA PT0-002 sample question which are the best for clearing PT0-002 test, and to get certified by CompTIA CompTIA PenTest+ Certification Exam. The PT0-002 Questions & Answers covers all the knowledge points of the real PT0-002 exam. Crack your CompTIA PT0-002 Exam with latest dumps, guaranteed!
Also have PT0-002 free dumps questions for you:
NEW QUESTION 1
Which of the following tools would be MOST useful in collecting vendor and other security-relevant information for IoT devices to support passive reconnaissance?
- A. Shodan
- B. Nmap
- C. WebScarab-NG
- D. Nessus
Answer: B
NEW QUESTION 2
Which of the following should a penetration tester do NEXT after identifying that an application being tested has already been compromised with malware?
- A. Analyze the malware to see what it does.
- B. Collect the proper evidence and then remove the malware.
- C. Do a root-cause analysis to find out how the malware got in.
- D. Remove the malware immediately.
- E. Stop the assessment and inform the emergency contact.
Answer: E
NEW QUESTION 3
A penetration tester discovered a vulnerability that provides the ability to upload to a path via directory traversal. Some of the files that were discovered through this vulnerability are: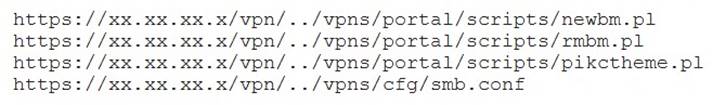
Which of the following is the BEST method to help an attacker gain internal access to the affected machine?
- A. Edit the discovered file with one line of code for remote callback
- B. Download .pl files and look for usernames and passwords
- C. Edit the smb.conf file and upload it to the server
- D. Download the smb.conf file and look at configurations
Answer: C
NEW QUESTION 4
Appending string values onto another string is called:
- A. compilation
- B. connection
- C. concatenation
- D. conjunction
Answer: C
NEW QUESTION 5
A penetration tester finds a PHP script used by a web application in an unprotected internal source code repository. After reviewing the code, the tester identifies the following: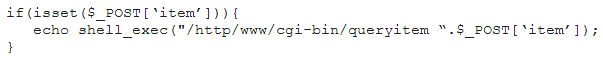
Which of the following tools will help the tester prepare an attack for this scenario?
- A. Hydra and crunch
- B. Netcat and cURL
- C. Burp Suite and DIRB
- D. Nmap and OWASP ZAP
Answer: C
NEW QUESTION 6
A penetration tester is scanning a corporate lab network for potentially vulnerable services. Which of the following Nmap commands will return vulnerable ports that might be interesting to a potential attacker?
- A. nmap192.168.1.1-5–PU22-25,80
- B. nmap192.168.1.1-5–PA22-25,80
- C. nmap192.168.1.1-5–PS22-25,80
- D. nmap192.168.1.1-5–Ss22-25,80
Answer: C
NEW QUESTION 7
A company becomes concerned when the security alarms are triggered during a penetration test. Which of the following should the company do NEXT?
- A. Halt the penetration test.
- B. Contact law enforcement.
- C. Deconflict with the penetration tester.
- D. Assume the alert is from the penetration test.
Answer: B
NEW QUESTION 8
A penetration tester exploited a unique flaw on a recent penetration test of a bank. After the test was completed, the tester posted information about the exploit online along with the IP addresses of the exploited machines. Which of the following documents could hold the penetration tester accountable for this action?
- A. ROE
- B. SLA
- C. MSA
- D. NDA
Answer: D
NEW QUESTION 9
When preparing for an engagement with an enterprise organization, which of the following is one of the MOST important items to develop fully prior to beginning the penetration testing activities?
- A. Clarify the statement of work.
- B. Obtain an asset inventory from the client.
- C. Interview all stakeholders.
- D. Identify all third parties involved.
Answer: A
NEW QUESTION 10
A penetration tester needs to perform a test on a finance system that is PCI DSS v3.2.1 compliant. Which of the following is the MINIMUM frequency to complete the scan of the system?
- A. Weekly
- B. Monthly
- C. Quarterly
- D. Annually
Answer: A
NEW QUESTION 11
A penetration-testing team is conducting a physical penetration test to gain entry to a building. Which of the following is the reason why the penetration testers should carry copies of the engagement documents with them?
- A. As backup in case the original documents are lost
- B. To guide them through the building entrances
- C. To validate the billing information with the client
- D. As proof in case they are discovered
Answer: D
NEW QUESTION 12
A client has requested that the penetration test scan include the following UDP services: SNMP, NetBIOS, and DNS. Which of the following Nmap commands will perform the scan?
- A. nmap –vv sUV –p 53, 123-159 10.10.1.20/24 –oA udpscan
- B. nmap –vv sUV –p 53,123,161-162 10.10.1.20/24 –oA udpscan
- C. nmap –vv sUV –p 53,137-139,161-162 10.10.1.20/24 –oA udpscan
- D. nmap –vv sUV –p 53, 122-123, 160-161 10.10.1.20/24 –oA udpscan
Answer: B
NEW QUESTION 13
Which of the following protocols or technologies would provide in-transit confidentiality protection for emailing the final security assessment report?
- A. S/MIME
- B. FTPS
- C. DNSSEC
- D. AS2
Answer: A
NEW QUESTION 14
A penetration tester runs the following command on a system:
find / -user root –perm -4000 –print 2>/dev/null
Which of the following is the tester trying to accomplish?
- A. Set the SGID on all files in the / directory
- B. Find the /root directory on the system
- C. Find files with the SUID bit set
- D. Find files that were created during exploitation and move them to /dev/null
Answer: C
NEW QUESTION 15
The results of an Nmap scan are as follows:
Starting Nmap 7.80 ( https://nmap.org ) at 2021-01-24 01:10 EST Nmap scan report for ( 10.2.1.22 )
Host is up (0.0102s latency). Not shown: 998 filtered ports Port State Service
80/tcp open http
|_http-title: 80F 22% RH 1009.1MB (text/html)
|_http-slowloris-check:
| VULNERABLE:
| Slowloris DoS Attack
| <..>
Device type: bridge|general purpose
Running (JUST GUESSING) : QEMU (95%)
OS CPE: cpe:/a:qemu:qemu
No exact OS matches found for host (test conditions non-ideal).
OS detection performed. Please report any incorrect results at https://nmap.org/submit/. Nmap done: 1 IP address (1 host up) scanned in 107.45 seconds
Which of the following device types will MOST likely have a similar response? (Choose two.)
- A. Network device
- B. Public-facing web server
- C. Active Directory domain controller
- D. IoT/embedded device
- E. Exposed RDP
- F. Print queue
Answer: AB
NEW QUESTION 16
A penetration tester runs a scan against a server and obtains the following output: 21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-12-20 09:23AM 331 index.aspx
| ftp-syst:
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds Microsoft Windows Server 2012 Std 3389/tcp open ssl/ms-wbt-server
| rdp-ntlm-info:
| Target Name: WEB3
| NetBIOS_Computer_Name: WEB3
| Product_Version: 6.3.9600
|_ System_Time: 2021-01-15T11:32:06+00:00
8443/tcp open http Microsoft IIS httpd 8.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/8.5
|_http-title: IIS Windows Server
Which of the following command sequences should the penetration tester try NEXT?
- A. ftp 192.168.53.23
- B. smbclient \\\\WEB3\\IPC$ -I 192.168.53.23 –U guest
- C. ncrack –u Administrator –P 15worst_passwords.txt –p rdp 192.168.53.23
- D. curl –X TRACE https://192.168.53.23:8443/index.aspx
- E. nmap –-script vuln –sV 192.168.53.23
Answer: A
NEW QUESTION 17
......
Thanks for reading the newest PT0-002 exam dumps! We recommend you to try the PREMIUM Dumps-hub.com PT0-002 dumps in VCE and PDF here: https://www.dumps-hub.com/PT0-002-dumps.html (110 Q&As Dumps)