A Review Of High Value PT0-002 Free Exam Questions
Ucertify PT0-002 Questions are updated and all PT0-002 answers are verified by experts. Once you have completely prepared with our PT0-002 exam prep kits you will be ready for the real PT0-002 exam without a problem. We have Updated CompTIA PT0-002 dumps study guide. PASSED PT0-002 First attempt! Here What I Did.
Free demo questions for CompTIA PT0-002 Exam Dumps Below:
NEW QUESTION 1
A company hired a penetration tester to do a social-engineering test against its employees. Although the tester did not find any employees’ phone numbers on the company’s website, the tester has learned the complete phone catalog was published there a few months ago.
In which of the following places should the penetration tester look FIRST for the employees’ numbers?
- A. Web archive
- B. GitHub
- C. File metadata
- D. Underground forums
Answer: A
NEW QUESTION 2
When developing a shell script intended for interpretation in Bash, the interpreter /bin/bash should be explicitly specified. Which of the following character combinations should be used on the first line of the script to accomplish this goal?
- A. <#
- B. <$
- C. ##
- D. #$
- E. #!
Answer: E
NEW QUESTION 3
Which of the following BEST describe the OWASP Top 10? (Choose two.)
- A. The most critical risks of web applications
- B. A list of all the risks of web applications
- C. The risks defined in order of importance
- D. A web-application security standard
- E. A risk-governance and compliance framework
- F. A checklist of Apache vulnerabilities
Answer: AC
NEW QUESTION 4
A penetration tester who is performing a physical assessment of a company’s security practices notices the company does not have any shredders inside the office building. Which of the following techniques would be BEST to use to gain confidential information?
- A. Badge cloning
- B. Dumpster diving
- C. Tailgating
- D. Shoulder surfing
Answer: B
NEW QUESTION 5
A penetration tester has been hired to configure and conduct authenticated scans of all the servers on a software company’s network. Which of the following accounts should the tester use to return the MOST results?
- A. Root user
- B. Local administrator
- C. Service
- D. Network administrator
Answer: C
NEW QUESTION 6
A penetration tester has been given eight business hours to gain access to a client’s financial system. Which of the following techniques will have the highest likelihood of success?
- A. Attempting to tailgate an employee going into the client's workplace
- B. Dropping a malicious USB key with the company’s logo in the parking lot
- C. Using a brute-force attack against the external perimeter to gain a foothold
- D. Performing spear phishing against employees by posing as senior management
Answer: C
NEW QUESTION 7
The results of an Nmap scan are as follows: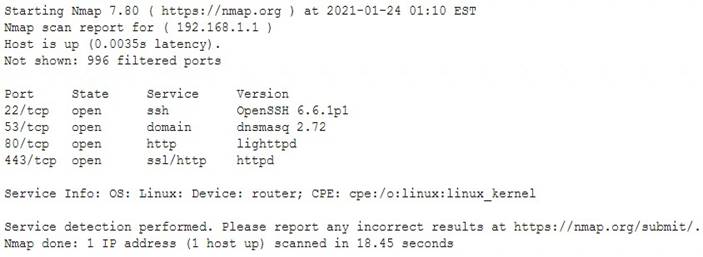
Which of the following would be the BEST conclusion about this device?
- A. This device may be vulnerable to the Heartbleed bug due to the way transactions over TCP/22 handle heartbeat extension packets, allowing attackers to obtain sensitive information from process memory.
- B. This device is most likely a gateway with in-band management services.
- C. This device is most likely a proxy server forwarding requests over TCP/443.
- D. This device may be vulnerable to remote code execution because of a butter overflow vulnerability in the method used to extract DNS names from packets prior to DNSSEC validation.
Answer: A
NEW QUESTION 8
A penetration tester who is doing a company-requested assessment would like to send traffic to another system using double tagging. Which of the following techniques would BEST accomplish this goal?
- A. RFID cloning
- B. RFID tagging
- C. Meta tagging
- D. Tag nesting
Answer: C
NEW QUESTION 9
A penetration tester who is conducting a web-application test discovers a clickjacking vulnerability associated with a login page to financial data. Which of the following should the tester do with this information to make this a successful exploit?
- A. Perform XSS.
- B. Conduct a watering-hole attack.
- C. Use BeEF.
- D. Use browser autopwn.
Answer: A
NEW QUESTION 10
A penetration tester is testing a web application that is hosted by a public cloud provider. The tester is able to query the provider’s metadata and get the credentials used by the instance to authenticate itself. Which of the following vulnerabilities has the tester exploited?
- A. Cross-site request forgery
- B. Server-side request forgery
- C. Remote file inclusion
- D. Local file inclusion
Answer: B
NEW QUESTION 11
A penetration tester runs the unshadow command on a machine. Which of the following tools will the tester most likely use NEXT?
- A. John the Ripper
- B. Hydra
- C. Mimikatz
- D. Cain and Abel
Answer: A
NEW QUESTION 12
A large client wants a penetration tester to scan for devices within its network that are Internet facing. The client is specifically looking for Cisco devices with no authentication requirements. Which of the following settings in Shodan would meet the client’s requirements?
- A. “cisco-ios” “admin+1234”
- B. “cisco-ios” “no-password”
- C. “cisco-ios” “default-passwords”
- D. “cisco-ios” “last-modified”
Answer: A
NEW QUESTION 13
Which of the following are the MOST important items to include in the final report for a penetration test?
(Choose two.)
- A. The CVSS score of the finding
- B. The network location of the vulnerable device
- C. The vulnerability identifier
- D. The client acceptance form
- E. The name of the person who found the flaw
- F. The tool used to find the issue
Answer: CF
NEW QUESTION 14
A penetration tester conducted an assessment on a web server. The logs from this session show the following:
http://www.thecompanydomain.com/servicestatus.php?serviceID=892&serviceID=892 ‘ ; DROP TABLE SERVICES; -
Which of the following attacks is being attempted?
- A. Clickjacking
- B. Session hijacking
- C. Parameter pollution
- D. Cookie hijacking
- E. Cross-site scripting
Answer: C
NEW QUESTION 15
A penetration tester recently performed a social-engineering attack in which the tester found an employee of the target company at a local coffee shop and over time built a relationship with the employee. On the employee’s birthday, the tester gave the employee an external hard drive as a gift. Which of the following social-engineering attacks was the tester utilizing?
- A. Phishing
- B. Tailgating
- C. Baiting
- D. Shoulder surfing
Answer: C
NEW QUESTION 16
A penetration tester logs in as a user in the cloud environment of a company. Which of the following Pacu modules will enable the tester to determine the level of access of the existing user?
- A. iam_enum_permissions
- B. iam_privesc_scan
- C. iam_backdoor_assume_role
- D. iam_bruteforce_permissions
Answer: A
NEW QUESTION 17
......
100% Valid and Newest Version PT0-002 Questions & Answers shared by Dumps-files.com, Get Full Dumps HERE: https://www.dumps-files.com/files/PT0-002/ (New 110 Q&As)