The Secret Of CompTIA CS0-002 Practice Question
Act now and download your CompTIA CS0-002 test today! Do not waste time for the worthless CompTIA CS0-002 tutorials. Download Abreast of the times CompTIA CompTIA Cybersecurity Analyst (CySA+) Certification Exam exam with real questions and answers and begin to learn CompTIA CS0-002 with a classic professional.
Free CS0-002 Demo Online For CompTIA Certifitcation:
NEW QUESTION 1
A cybersecurity analyst is responding to an incident. The company’s leadership team wants to attribute the incident to an attack group. Which of the following models would BEST apply to the situation?
- A. Intelligence cycle
- B. Diamond Model of Intrusion Analysis
- C. Kill chain
- D. MITRE ATT&CK
Answer: B
NEW QUESTION 2
When attempting to do a stealth scan against a system that does not respond to ping, which of the following Nmap commands BEST accomplishes that goal?
- A. nmap –sA –O <system> -noping
- B. nmap –sT –O <system> -P0
- C. nmap –sS –O <system> -P0
- D. nmap –sQ –O <system> -P0
Answer: C
NEW QUESTION 3
It is important to parameterize queries to prevent:
- A. the execution of unauthorized actions against a database.
- B. a memory overflow that executes code with elevated privileges.
- C. the establishment of a web shell that would allow unauthorized access.
- D. the queries from using an outdated library with security vulnerabilities.
Answer: A
NEW QUESTION 4
A threat feed notes malicious actors have been infiltrating companies and exfiltration data to a specific set of domains Management at an organization wants to know if it is a victim Which of the following should the security analyst recommend to identity this behavior without alerting any potential malicious actors?
- A. Create an IPS rule to block these domains and trigger an alert within the SIEM tool when these domains are requested
- B. Add the domains to a DNS sinkhole and create an alert m the SIEM toot when the domains are queried
- C. Look up the IP addresses for these domains and search firewall logs for any traffic being sent to those IPs over port 443
- D. Query DNS logs with a SIEM tool for any hosts requesting the malicious domains and create alerts based on this information
Answer: D
NEW QUESTION 5
A security analyst received an email with the following key: Xj3XJ3LLc
A second security analyst received an email with following key: 3XJ3xjcLLC
The security manager has informed the two analysts that the email they received is a key that allows access to the company’s financial segment for maintenance. This is an example of:
- A. dual control
- B. private key encryption
- C. separation of duties
- D. public key encryption
- E. two-factor authentication
Answer: A
NEW QUESTION 6
A monthly job to install approved vendor software updates and hot fixes recently stopped working. The security team performed a vulnerability scan, which identified several hosts as having some critical OS vulnerabilities, as referenced in the common vulnerabilities and exposures (CVE) database.
Which of the following should the security team do NEXT to resolve the critical findings in the most effective manner? (Choose two.)
- A. Patch the required hosts with the correct updates and hot fixes, and rescan them for vulnerabilities.
- B. Remove the servers reported to have high and medium vulnerabilities.
- C. Tag the computers with critical findings as a business risk acceptance.
- D. Manually patch the computers on the network, as recommended on the CVE website.
- E. Harden the hosts on the network, as recommended by the NIST framework.
- F. Resolve the monthly job issues and test them before applying them to the production network.
Answer: CE
NEW QUESTION 7
A security team wants to make SaaS solutions accessible from only the corporate campus.
Which of the following would BEST accomplish this goal?
- A. Geofencing
- B. IP restrictions
- C. Reverse proxy
- D. Single sign-on
Answer: A
NEW QUESTION 8
An analyst is working with a network engineer to resolve a vulnerability that was found in a piece of legacy hardware, which is critical to the operation of the organization's production line. The legacy hardware does not have third-party support, and the OEM manufacturer of the controller is no longer in operation. The analyst documents the activities and verifies these actions prevent remote exploitation of the vulnerability.
Which of the following would be the MOST appropriate to remediate the controller?
- A. Segment the network to constrain access to administrative interfaces.
- B. Replace the equipment that has third-party support.
- C. Remove the legacy hardware from the network.
- D. Install an IDS on the network between the switch and the legacy equipment.
Answer: A
NEW QUESTION 9
A security analyst is reviewing the following log from an email security service.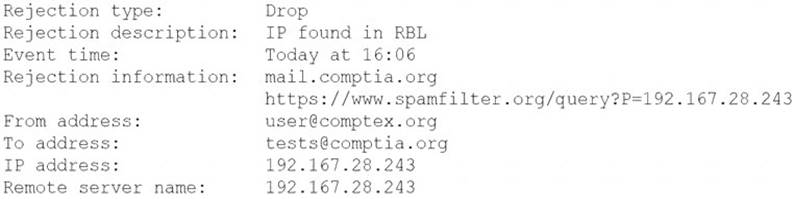
Which of the following BEST describes the reason why the email was blocked?
- A. The To address is invalid.
- B. The email originated from the www.spamfilter.org URL.
- C. The IP address and the remote server name are the same.
- D. The IP address was blacklisted.
- E. The From address is invalid.
Answer: D
NEW QUESTION 10
During an investigation, an incident responder intends to recover multiple pieces of digital media. Before removing the media, the responder should initiate:
- A. malware scans.
- B. secure communications.
- C. chain of custody forms.
- D. decryption tools.
Answer: C
NEW QUESTION 11
Bootloader malware was recently discovered on several company workstations. All the workstations run Windows and are current models with UEFI capability.
Which of the following UEFI settings is the MOST likely cause of the infections?
- A. Compatibility mode
- B. Secure boot mode
- C. Native mode
- D. Fast boot mode
Answer: A
NEW QUESTION 12
Which of the following MOST accurately describes an HSM?
- A. An HSM is a low-cost solution for encryption.
- B. An HSM can be networked based or a removable USB
- C. An HSM is slower at encrypting than software
- D. An HSM is explicitly used for MFA
Answer: A
NEW QUESTION 13
A user's computer has been running slowly when the user tries to access web pages. A security analyst runs the command netstat -aon from the command line and receives the following output: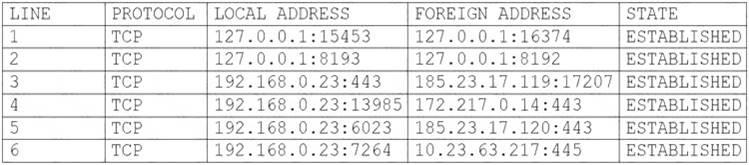
Which of the following lines indicates the computer may be compromised?
- A. Line 1
- B. Line 2
- C. Line 3
- D. Line 4
- E. Line 5
- F. Line 6
Answer: D
NEW QUESTION 14
An information security analyst is reviewing backup data sets as part of a project focused on eliminating archival data sets.
Which of the following should be considered FIRST prior to disposing of the electronic data?
- A. Sanitization policy
- B. Data sovereignty
- C. Encryption policy
- D. Retention standards
Answer: D
NEW QUESTION 15
A security analyst is investigating a malware infection that occurred on a Windows system. The system was not connected to a network and had no wireless capability Company policy prohibits using portable media or mobile storage The security analyst is trying to determine which user caused the malware to get onto the system Which of the following registry keys would MOST likely have this information?
A)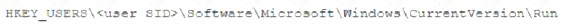
B)
C)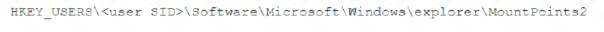
D)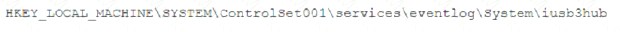
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: C
NEW QUESTION 16
An organization has not had an incident for several month. The Chief information Security Officer (CISO) wants to move to proactive stance for security investigations. Which of the following would BEST meet that goal?
- A. Root-cause analysis
- B. Active response
- C. Advanced antivirus
- D. Information-sharing community
- E. Threat hunting
Answer: E
NEW QUESTION 17
......
P.S. 2passeasy now are offering 100% pass ensure CS0-002 dumps! All CS0-002 exam questions have been updated with correct answers: https://www.2passeasy.com/dumps/CS0-002/ (186 New Questions)