Breathing 412-79v10 Torrent 2021
Cause all that matters here is passing the EC-Council 412-79v10 exam. Cause all that you need is a high score of 412-79v10 EC-Council Certified Security Analyst (ECSA) V10 exam. The only one thing you need to do is downloading Actualtests 412-79v10 exam study guides now. We will not let you down with our money-back guarantee.
NEW QUESTION 1
Which Wireshark filter displays all the packets where the IP address of the source host is 10.0.0.7?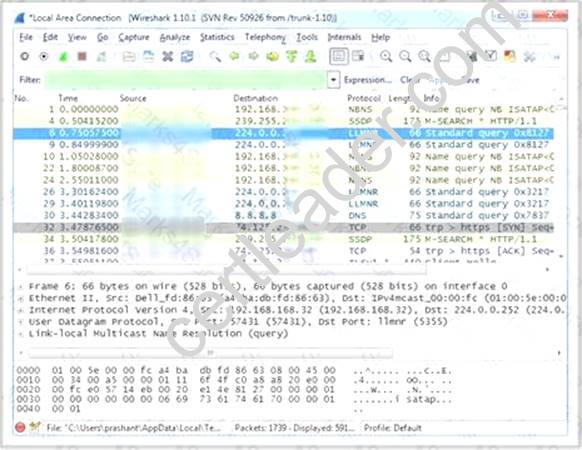
- A. ip.dst==10.0.0.7
- B. ip.port==10.0.0.7
- C. ip.src==10.0.0.7
- D. ip.dstport==10.0.0.7
Answer: C
NEW QUESTION 2
Which of the following equipment could a pen tester use to perform shoulder surfing?
- A. Binoculars
- B. Painted ultraviolet material
- C. Microphone
- D. All the above
Answer: A
NEW QUESTION 3
After passively scanning the network of Department of Defense (DoD), you switch over to active scanning to identify live hosts on their network. DoD is a large organization and should respond to any number of scans. You start an ICMP ping sweep by sending an IP packet to the broadcast address.
Only five hosts responds to your ICMP pings; definitely not the number of hosts you were expecting. Why did this ping sweep only produce a few responses?
- A. A switched network will not respond to packets sent to the broadcast address
- B. Only IBM AS/400 will reply to this scan
- C. Only Unix and Unix-like systems will reply to this scan
- D. Only Windows systems will reply to this scan
Answer: C
NEW QUESTION 4
Frank is working on a vulnerability assessment for a company on the West coast. The company hired Frank to assess its network security through scanning, pen tests, and vulnerability assessments. After discovering numerous known vulnerabilities detected by a temporary IDS he set up, he notices a number of items that show up as unknown but questionable in the logs.
He looks up the behavior on the Internet, but cannot find anything related. What organization should Frank submit the log to find out if it is a new vulnerability or not?
- A. CVE
- B. IANA
- C. RIPE
- D. APIPA
Answer: A
NEW QUESTION 5
An antenna is a device that is designed to transmit and receive the electromagnetic waves that are generally called radio waves. Which one of the following types of antenna is developed from waveguide technology?
- A. Leaky Wave Antennas
- B. Aperture Antennas
- C. Reflector Antenna
- D. Directional Antenna
Answer: B
NEW QUESTION 6
What is a difference between host-based intrusion detection systems (HIDS) and network-based intrusion detection systems (NIDS)?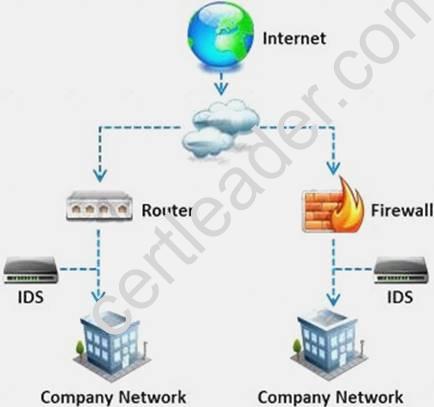
- A. NIDS are usually a more expensive solution to implement compared to HIDS.
- B. Attempts to install Trojans or backdoors cannot be monitored by a HIDS whereas NIDS can monitor and stop such intrusion events.
- C. NIDS are standalone hardware appliances that include network intrusion detection capabilities whereas HIDS consist of software agents installed on individual computers within the system.
- D. HIDS requires less administration and training compared to NIDS.
Answer: C
NEW QUESTION 7
Wireless communication allows networks to extend to places that might otherwise go untouched by the wired networks. When most people say ‘Wireless’ these days, they are referring to one of the 802.11 standards. There are three main 802.11 standards: B, A, and G.
Which one of the following 802.11 types uses DSSS Modulation, splitting the 2.4ghz band into channels?
- A. 802.11b
- B. 802.11g
- C. 802.11-Legacy
- D. 802.11n
Answer: A
NEW QUESTION 8
Snort, an open source network-based intrusion detection sensor, is the most widely installed NIDS in the world. It can be configured to run in the four modes. Which one of the following modes reads the packets off the network and displays them in a continuous stream on the console (screen)?
- A. Packet Sniffer Mode
- B. Packet Logger Mode
- C. Network Intrusion Detection System Mode
- D. Inline Mode
Answer: A
NEW QUESTION 9
An automated electronic mail message from a mail system which indicates that the user does not exist on that server is called as?
- A. SMTP Queue Bouncing
- B. SMTP Message Bouncing
- C. SMTP Server Bouncing
- D. SMTP Mail Bouncing
Answer: D
NEW QUESTION 10
Timing is an element of port-scanning that can catch one unaware. If scans are taking too long to complete or obvious ports are missing from the scan, various time parameters may need to be adjusted.
Which one of the following scanned timing options in NMAP’s scan is useful across slow WAN links or to hide the scan?
- A. Paranoid
- B. Sneaky
- C. Polite
- D. Normal
Answer: C
NEW QUESTION 11
Identify the type of testing that is carried out without giving any information to the employees or
administrative head of the organization.
- A. Unannounced Testing
- B. Double Blind Testing
- C. Announced Testing
- D. Blind Testing
Answer: B
NEW QUESTION 12
George is the network administrator of a large Internet company on the west coast. Per corporate policy, none of the employees in the company are allowed to use FTP or SFTP programs without obtaining approval from the IT department. Few managers are using SFTP program on their computers.
Before talking to his boss, George wants to have some proof of their activity. George wants to use Ethereal t monitor network traffic, but only SFTP traffic to and from his network. What filter should George use in Ethereal?
- A. net port 22
- B. udp port 22 and host 172.16.28.1/24
- C. src port 22 and dst port 22
- D. src port 23 and dst port 23
Answer: C
NEW QUESTION 13
Which of the following shields Internet users from artificial DNS data, such as a deceptive or mischievous address instead of the genuine address that was requested?
- A. DNSSEC
- B. Firewall
- C. Packet filtering
- D. IPSec
Answer: A
NEW QUESTION 14
An attacker injects malicious query strings in user input fields to bypass web service authentication mechanisms and to access back-end databases. Which of the following attacks is this?
- A. Frame Injection Attack
- B. LDAP Injection Attack
- C. XPath Injection Attack
- D. SOAP Injection Attack
Answer: D
NEW QUESTION 15
Which of the following contents of a pen testing project plan addresses the strengths, weaknesses, opportunities, and threats involved in the project?
- A. Project Goal
- B. Success Factors
- C. Objectives
- D. Assumptions
Answer: D
NEW QUESTION 16
You are trying to locate Microsoft Outlook Web Access Default Portal using Google search on the Internet. What search string will you use to locate them?
- A. intitle:"exchange server"
- B. outlook:"search"
- C. locate:"logon page"
- D. allinurl:"exchange/logon.asp"
Answer: D
NEW QUESTION 17
Which of the following is the objective of Gramm-Leach-Bliley Act?
- A. To ease the transfer of financial information between institutions and banks
- B. To protect the confidentiality, integrity, and availability of data
- C. To set a new or enhanced standards for all U.
- D. public company boards, management and public accounting firms
- E. To certify the accuracy of the reported financial statement
Answer: A
NEW QUESTION 18
Jessica works as systems administrator for a large electronics firm. She wants to scan her network quickly to detect live hosts by using ICMP ECHO Requests. What type of scan is Jessica going to perform?
- A. Smurf scan
- B. Tracert
- C. Ping trace
- D. ICMP ping sweep
Answer: D
NEW QUESTION 19
One needs to run “Scan Server Configuration” tool to allow a remote connection to Nessus from the remote Nessus clients. This tool allows the port and bound interface of the Nessus daemon to be configured.
By default, the Nessus daemon listens to connections on which one of the following?
- A. Localhost (127.0.0.1) and port 1241
- B. Localhost (127.0.0.1) and port 1240
- C. Localhost (127.0.0.1) and port 1246
- D. Localhost (127.0.0.0) and port 1243
Answer: A
NEW QUESTION 20
War Driving is the act of moving around a specific area, mapping the population of wireless access points for statistical purposes. These statistics are then used to raise awareness of the security problems associated with these types of networks.
Which one of the following is a Linux based program that exploits the weak IV (Initialization Vector) problem
documented with static WEP?
- A. Airsnort
- B. Aircrack
- C. WEPCrack
- D. Airpwn
Answer: A
NEW QUESTION 21
Vulnerability assessment is an examination of the ability of a system or application, including the current security procedures and controls, to withstand assault.
What does a vulnerability assessment identify?
- A. Disgruntled employees
- B. Weaknesses that could be exploited
- C. Physical security breaches
- D. Organizational structure
Answer: B
NEW QUESTION 22
Which of the following acts related to information security in the US establish that the management of an organization is responsible for establishing and maintaining an adequate internal control structure and procedures for financial reporting?
- A. USA Patriot Act 2001
- B. Sarbanes-Oxley 2002
- C. Gramm-Leach-Bliley Act (GLBA)
- D. California SB 1386
Answer: A
NEW QUESTION 23
When you are running a vulnerability scan on a network and the IDS cuts off your connection, what type of IDS is being used?
- A. Passive IDS
- B. Active IDS
- C. Progressive IDS
- D. NIPS
Answer: B
NEW QUESTION 24
In Linux, /etc/shadow file stores the real password in encrypted format for user’s account with added properties associated with the user’s password.
In the example of a /etc/shadow file below, what does the bold letter string indicate?
Vivek: $1$fnffc$GteyHdicpGOfffXX40w#5:13064:0:99999:7
- A. Number of days the user is warned before the expiration date
- B. Minimum number of days required between password changes
- C. Maximum number of days the password is valid
- D. Last password changed
Answer: B
NEW QUESTION 25
The term social engineering is used to describe the various tricks used to fool people (employees, business partners, or customers) into voluntarily giving away information that would not normally be known to the general public.
What is the criminal practice of social engineering where an attacker uses the telephone system in an attempt to scam the user into surrendering private information?
- A. Phishing
- B. Spoofing
- C. Tapping
- D. Vishing
Answer: D
NEW QUESTION 26
ARP spoofing is a technique whereby an attacker sends fake ("spoofed") Address Resolution Protocol (ARP) messages onto a Local Area Network. Generally, the aim is to associate the attacker's MAC address with the IP address of another host (such as the default gateway), causing any traffic meant for that IP address to be sent to the attacker instead.
ARP spoofing attack is used as an opening for other attacks.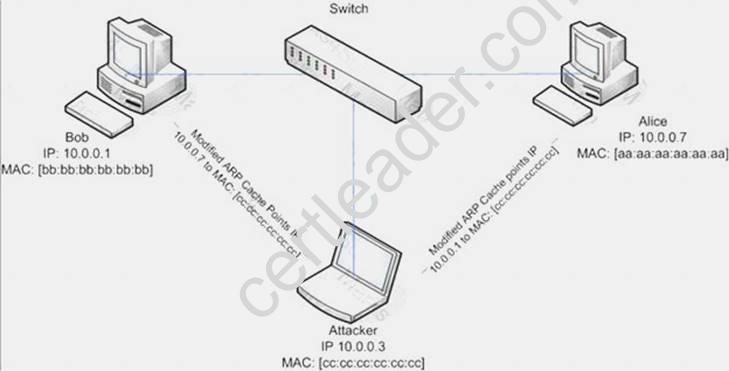
What type of attack would you launch after successfully deploying ARP spoofing?
- A. Parameter Filtering
- B. Social Engineering
- C. Input Validation
- D. Session Hijacking
Answer: D
NEW QUESTION 27
As a security analyst you setup a false survey website that will require users to create a username and a strong password. You send the link to all the employees of the company. What information will you be able to gather?
- A. The employees network usernames and passwords
- B. The MAC address of the employees' computers
- C. The IP address of the employees computers
- D. Bank account numbers and the corresponding routing numbers
Answer: C
NEW QUESTION 28
You are assisting a Department of Defense contract company to become compliant with the stringent
security policies set by the DoD. One such strict rule is that firewalls must only allow incoming connections that were first initiated by internal computers.
What type of firewall must you implement to abide by this policy?
- A. Circuit-level proxy firewall
- B. Packet filtering firewall
- C. Application-level proxy firewall
- D. Statefull firewall
Answer: D
NEW QUESTION 29
Which among the following information is not furnished by the Rules of Engagement (ROE) document?
- A. Techniques for data collection from systems upon termination of the test
- B. Techniques for data exclusion from systems upon termination of the test
- C. Details on how data should be transmitted during and after the test
- D. Details on how organizational data is treated throughout and after the test
Answer: A
NEW QUESTION 30
An "idle" system is also referred to as what?
- A. Zombie
- B. PC not being used
- C. Bot
- D. PC not connected to the Internet
Answer: A
NEW QUESTION 31
......
P.S. Easily pass 412-79v10 Exam with 201 Q&As Certifytools Dumps & pdf Version, Welcome to Download the Newest Certifytools 412-79v10 Dumps: https://www.certifytools.com/412-79v10-exam.html (201 New Questions)